Corporate Cyber Protection and Management - Integrated platform for end-of-life protection, identity protection and cloud protection
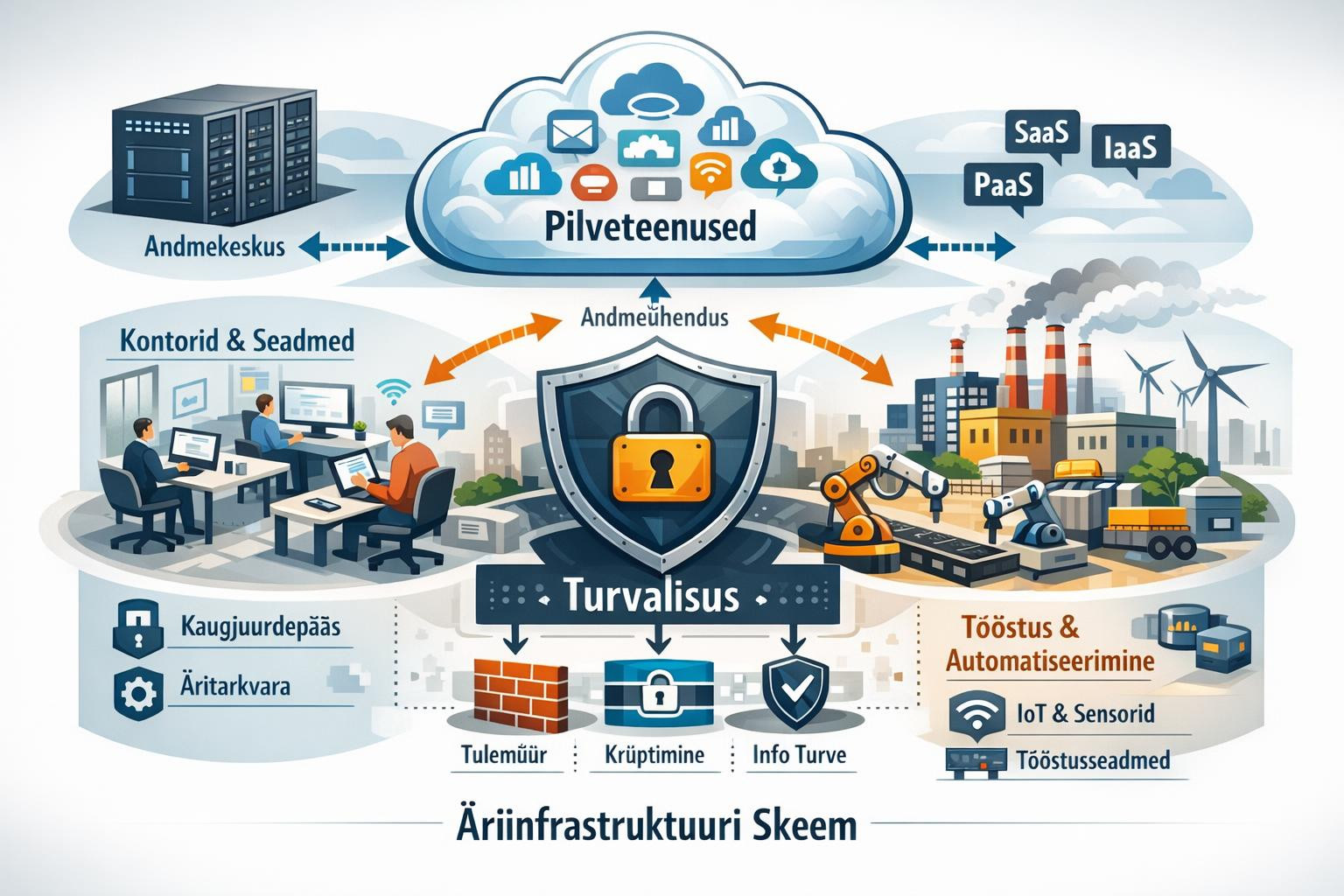
The Single Administrative Platform combines the final point, identity and data protection into one manageable solution to reduce the diversification of tools and increase visibility throughout the organisation. Thanks to clear operational control of attack surfaces and continuous support, you can react faster and recover from attacks with reduced stagnation time.
What is the core of the solution?
The platform integrates end-point protection, identification protection and cloud protection with central control panels that provide real-time overview of risks, discoveries and responsibilities. Automatic orchestration and consistent rules simplify administration and reduce the number of manual operations.
Who is this suitable for?
For large companies, distributed IT teams, service providers (MSPs) and organisations that require stronger visibility, control and speed in response to security incidents. Suitable especially for areas where requirements for compliance, data protection and reduction of workstations are high.
Principal functions and advantages
- <Final point of contact protection: continuous protection of terminal equipment, due diligence checks and automatic attack prevention reduce the risk of infection.
- Identitic protection: protection, multi-level authentication and detection of anomalies protects against unauthorised access.
- Pilve protection: constant monitoring of configuration of configurations and data in cloud environments, the possibility to quickly close off vulnerable parts of surface. >>rong>Ces The central control panels allow drivers and security teams to make decisions on a data-based basis, while automation keeps operational work smooth.
- Connected workflows: end-point, identity and cloud-level data work together that detects more complex attack patterns.
- Skalatable architecture: growth-related safeguards and management tools without further complexity.
- Li>Continuous service and customary repair procedures: support received during incidents reduces stagnations and accelerates recovery.
- Compatibility and audits: standardised policies and detailed traceability facilitate verification of compliance. /l>
Differences that count
How the introduction supports business objectives
/h2> The simplification of security management The approach supports faster innovation because risk management is integrated and visible to all decision makers.Take control over: single platform ensures that security decisions are based on real data, response is automatic and recovery controlled - all necessary from one central platform.






Comments (0)